The Easy Guide to Setting Up an Efficient Virtual Call Center

Setting up a virtual call center? It’s simpler and quicker than you think. Many people spend too much time trying to perfect every aspect. The best plan? Dive in and learn through experience. Here’s how you can start a virtual call center in four steps—five if you need to hire. Step 1: Lay the Foundation […]
NVIDIA Unveils New Mini Developer Kit for Generative AI

NVIDIA just launched an exciting new supercomputer for home use – the Jetson Orin Nano Super Developer Kit, right in time for the holidays. This platform pushes generative AI performance by 70% compared to its predecessor, making it a solid choice for developers and hobbyists keen on training AI tools, agents, and robots. If you […]
Step-by-Step Guide to Locating Your Network Security Key on Any Device

Are you trying to locate your network security key? You’re in good company. Here’s a straightforward guide to help you find it on the four most common devices. Quick Overview iOS: Open the Settings app, tap Wi-Fi, select your network, and check the Password field. Android: Go to Settings, tap Network & Internet, choose Internet, […]
5 Benefits of Implementing a Stateless Firewall (and 3 Important Limitations)

In networking, “state” means the context of your current connection. A stateful firewall tracks each connection’s status, while a stateless firewall does not. Though they may seem less complex, stateless firewalls are great for securing home and business networks. They use access control lists (ACLs) to determine which traffic gets through and which doesn’t. Stateless […]
Which Linux Distribution Is Right for You?

If you’ve talked to a Linux veteran about the best desktop distribution for new users, you’ve probably heard the name Ubuntu come up. The same goes for server distributions, where Debian often joins the conversation. Debian and Ubuntu are both solid, free Linux options. There’s no definitive winner between the two. But if you’re looking […]
Ubuntu Server Quick Reference Guide

Ubuntu Server is a powerful, free, and open-source operating system that can handle a wide range of tasks. Whether you need an internal server or something that can scale for enterprise-level demands, Ubuntu is versatile enough to meet those needs. This guide serves as your quick reference for Ubuntu Server. We’ll keep it updated as […]
Understanding Sales Automation: Tips and Examples

Sales automation is one of the key features of top CRM software. You’ll see it in action across the sales process—from generating and scoring leads to setting up meetings and forecasting results. By automating these tasks, sales reps can spend more time engaging with customers and closing deals. So what exactly is sales automation? It’s […]
Managing Services in Linux: Starting, Stopping, and Restarting

For advanced Linux users, managing services is a key skill. If you want to use a web server, like Apache, you need to start that service. To access a database, you’ll need to start MySQL. Effectively managing these services not only makes them accessible but also keeps your system stable and performing well. Many users […]
7 Time-Saving Free Marketing Campaign Templates You’ll Love
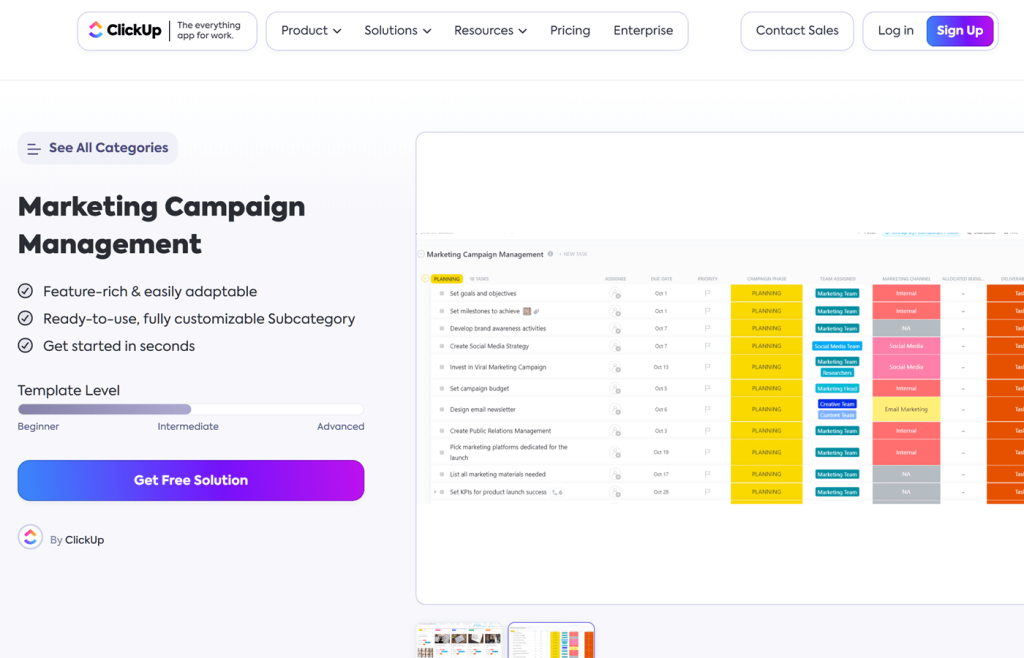
Marketing campaign templates give you the structure and clarity you need for your upcoming initiatives. They help keep your campaigns on track with your overarching goals and offer a detailed plan for execution, tracking, and measuring results. Whether it’s a quick one-time email or a long-running campaign across multiple channels, templates can simplify your approach. […]
OpenAI Unveils ChatGPT Search, A Direct Rival to Google
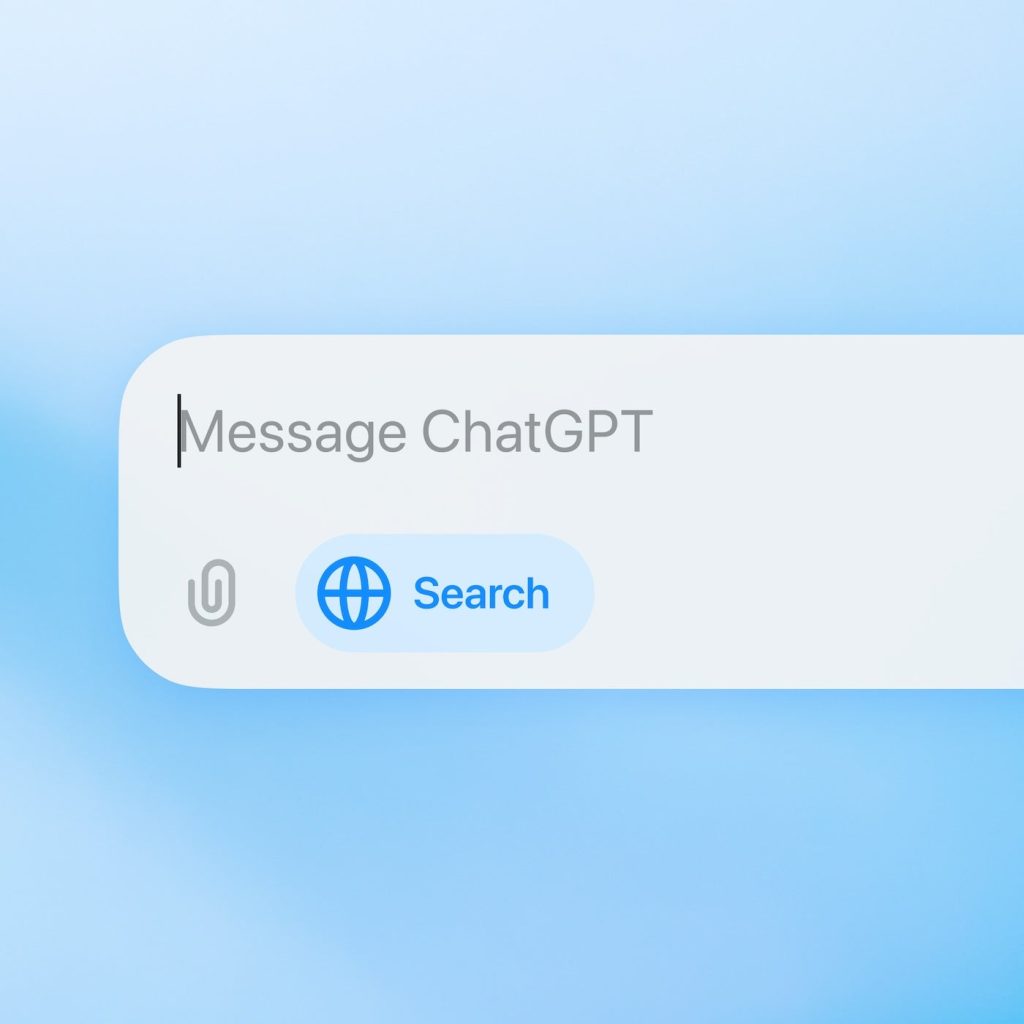
Starting today, OpenAI’s generative search engine is available to ChatGPT Plus subscribers, Team subscribers, and SearchGPT waitlist members, as announced on October 31. This development could rattle Google Search, as OpenAI aims to attract users away from Google’s platform. They’ve even created a Chrome extension to make ChatGPT the default search engine. This new search […]
